Vulnerability Management
Agentless and Cloud-Native Vulnerability Management
Uncover vulnerabilities across your clouds and workloads (VMs, Serverless, Containers, Appliances) without deploying agents or configuring external scans.
The Wiz Way
Fix Vulnerabilities at the Scale and Speed of the Cloud
Uncover blind spots, eliminate never-ending agent enforcement, and prioritize vulnerabilities by environmental risk.
Agentless
Using a one-time cloud native API deployment, continuously assess workloads without deploying agents.
Deep assessment
Detect every hidden nested log4j dependency or CISA KEV exploitable vulnerability across virtual machines, containers, container registries, serverless functions (Lambda), and virtual appliances.
Contextual risk-based prioritization
Prioritize remediation by focusing first on the resources that are effectively exposed or have the largest blast radius.
Go Beyond Agents and Scanners
Wiz's agentless scanning technology provides complete vulnerability visibility using a single cloud-native API connector to continuously assess workloads without needing any ongoing maintenance. Cross Cloud: Single pane of glass for vulnerability assessment across AWS, GCP, Azure, OCI, Alibaba Cloud, EKS, GKE, OKE and AKS. Cross Technology: Get a comprehensive assessment across virtual machines, ephemeral eesources (Auto-Scaling Groups), containers, container registries, serverless functions, virtual appliances (e.g. third-party firewalls) and managed compute resources (EMR clusters, GCP Dataprocs). 70K+ Supported Vulnerabilities: Our industry-leading vulnerability catalog consists of more than 70,000 supported vulnerabilities, across 30+ operating systems, CISA KEV catalog and thousands of applications.
Quickly Identify Emerging Threats
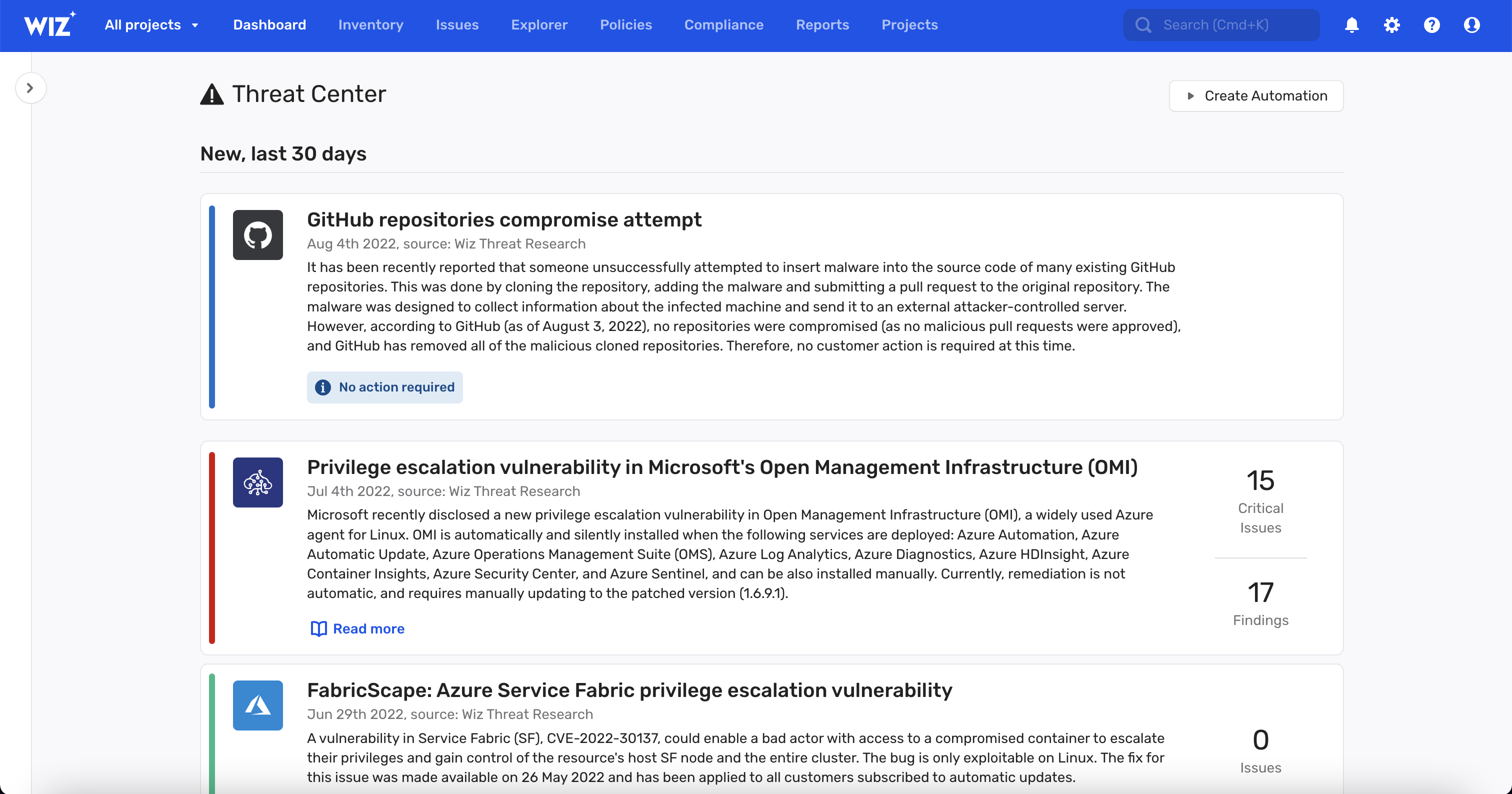
Threat Center: Use the Threat Center to immediately identify workload exposure to the latest vulnerabilities sourced from Wiz Research along with numerous third-party threat intelligence feeds. Take remediation action with a single click or via automation rules. <24hr Detection: High-profile vulnerabilities are continuously monitored by Wiz's research team. Detections are added on average less than 24 hours from disclosure.
Contextual Risk-Based Prioritization
Reduce alert fatigue by correlating vulnerabilities with multiple risk factors, including external exposure, cloud entitlements, secrets, misconfigurations, malware, and more, to surface the vulnerabilities that should be prioritized.
Scan Before Deployment

Agentless Host Configuration Analysis
Continuously monitor operating systems and application configurations according to CIS benchmarks (CIS Ubuntu, Red Hat, Windows, and more) without any agents or external scans.
Getting started is easy
Complete security for AWS, Azure, GCP, OCI, Alibaba Cloud, Kubernetes, and Openshift. Start securing your cloud with a 5 minute agentless install. Meet your new partner in cloud security.